Is cyber resilience the new conversation starter?
While the phrase ‘may you live in interesting times’ is widely regarded as an ancient Chinese curse, it was, in fact, said in 1939 by the American politician Frederic R. Coudert.
But, given the last few years, we all appreciate the sentiment regardless of where it originated.
The curse of cybercrime
Yes, these are interesting – and challenging times. And as discussed in the latest (July 2021-June 2022) ASCSC Annual Cyber Threat Report, it’s been an increasingly steep learning curve for many individuals, businesses and public and private sector organisations.
Australia is far from alone in being subjected to an unrelenting barrage of cyber-attacks, but obviously, it’s very close to home for us. And Victoria and Queensland, in particular, have reported disproportionately higher cybercrime rates relative to population size.
In the period covered by the report, ACSC responded to over 1,100 cybersecurity incidents. The sharp-eyed may spot that this is a 36% decrease in reported incidents over the previous year. However, ASCS suggest that the growth of Australia’s commercial incident response sector means that incidents they may have previously responded to are now being handled internally or by contracted incident response teams.
The cost of cybercrime
According to ACSC, the average cost to cybercrime-impacted Australian businesses is significant:
- For a small business with 1-20 employees, the average cost of an attack is $39,555
- For a medium business with 20-199 employees, expect to lose $88,407
- And those large businesses, with 200+ employees, should anticipate writing off $62,233
Yet, considering the significant damage that stolen data can cause, it’s surprisingly cheap to acquire if you’re on the dark side. Visual Capitalist recently shared a price list for dark web data.
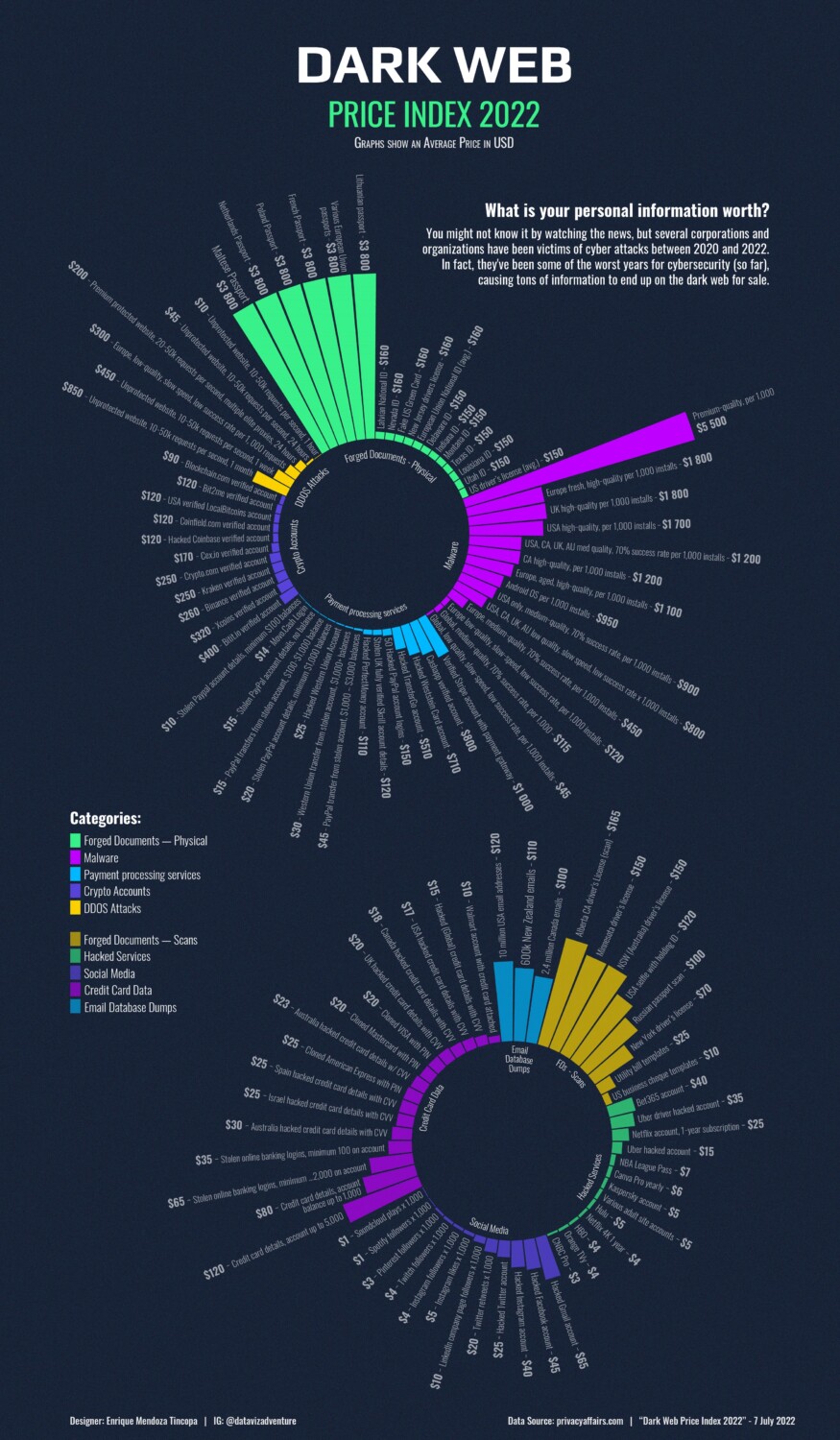
While passports remain a high-end investment (US$3800), an NSW Driver’s License can be had for US$150, and an Australian credit card, complete with CVV, is a mere snip at US$23.
As Brad, in the cult classic movie The Rocky Horror Picture Show, observed: “Life’s pretty cheap to that type.”
The hot cybercrime critical infrastructure sectors
ACSC says that 75% of all reported cybersecurity incidents in the 2021-2022 financial year were from the top 10 reporting sectors. Probably to their great relief, the retail sector is no longer part of that top 10, having been ousted by the electricity, gas, water and waste service sector.
The top three sectors under attack are the Commonwealth Government, which reported 24% of all incidents, followed by State/Territory/Local Government with 10% (although it must be noted that government sectors do have additional and more rigorous reporting obligations), and Health Care and Social Assistance at 9%.
The remaining seven top 10 sectors range from telecommunications to education, construction to manufacturing, and financial services to electricity, gas, water and waste services.
This ‘hot’ top 10 list makes the Australian Government’s Security Legislation Amendment (Critical Infrastructure Protection) Act 2022 even more relevant and timely. It places further security obligations on specific entities in the electricity, communications, data storage or processing, financial services and markets, water, health care and medical, higher education and research, food and grocery, transport, space technology, and defence industry – and their data centre and cloud service providers.
Notably, the bill not only aims to protect critical infrastructure organisations from cyberattacks but to enable rapid recovery through cyber resiliency.
And what about business email compromise?
ACSC’s new annual report also focuses on the highly lucrative area of BEC (business email compromise), and with good cause.
BEC is a strategy used by malicious actors to compromise organisations via email to scam businesses out of money or goods and trick employees into revealing confidential business information. And it’s also an entry point for malicious actors to move their focus to higher-value targets within business or organisation networks. A single compromised employee email can lead to a significant ransomware attack.
While ACSC says the number of BEC attacks declined in the 2021-2022 period, the average loss incurred per successful BEC increased to an Australian average of over $64,000. Unfortunately for Western Australians, their higher-than-average loss was $112,000 per report.
Property settlements have been a popular target due to the high value of transactions. You may remember the high-profile case of MasterChef contestant Dani Venn who lost (then thankfully recovered) $250,000 when PEXA (Property Exchange Australia), the online conveyancing giant, was hacked. This 2018 case was a wake-up call for many.
Ransomware: Here, there, and everywhere
Ransomware attacks were both high-profile and ubiquitous over the 2021-2022 period, reports ACSC. No sector was left untouched. Reported attacks were down, but ACSC states that it’s likely that they were significantly under-reported as victims instead chose to pay the ransom in an effort to return to a business-as-usual state ASAP.
The top five sectors under attack included education and training, information media and telecoms, State/Territory/Local Government and Health Care and Social Assistance.
Why does this all make cyber resilience a more important conversation than ever before?
We’ve discussed cyber resilience before. It’s something we’re passionate about. And at the risk of repeating ourselves (and if you don’t have time to read our earlier blog), here’s a quick recap of the difference between cybersecurity and cyber resilience:
Cybersecurity is how you protect your electronic data. It encompasses the processes, best business practices and technology solutions you put in place to safeguard your systems and network.
Cyber resiliency is your ability to prepare for, respond to, and recover from a cyberattack. If you’re cyber resilient, you’re better equipped to defend your organisation from attack, limit the impact on your systems and data, and continue working during and after an attack.
Cyber resiliency isn’t a conversation that will go away anytime soon. And nor should it.
ACSC has taken the topic seriously with initiatives like AquaEx (a national cyber security exercise series in partnership with Australia’s urban water and wastewater sector and government agencies), which have helped participating industries and government to work together to strengthen cyber resilience across Australia.
And following the Federal Court of Australia finding that financial planning company RI Advice has breached its financial services license by having inadequate cybersecurity risk management systems, ACSC said: “…it is a strong reminder that company boards should consider cyber resilience as part of their statutory responsibilities.”
Finally, ACSC says, and we quote, that “Australia’s best defence in a rapidly evolving cyber threat environment is to build resilience across businesses and organisations, and among individuals.”
And we couldn’t agree more.






